When people first hear about NSX-T, they usually think “overlay networking and firewalls”. That’s true, but incomplete. In real environments, NSX-T quickly becomes a control plane for how applications are allowed to exist.
The moment you introduce Distributed Firewall (DFW), networking stops being something that only network teams touch. Security, application owners, and even automation pipelines start to care.
A classic 3-tier application: WEB VMs -> APP VMs -> DB VMs
Traditional setup: 3 VLANs; Perimeter firewall rules; Broad “allow” rules inside the data center
With NSX-T
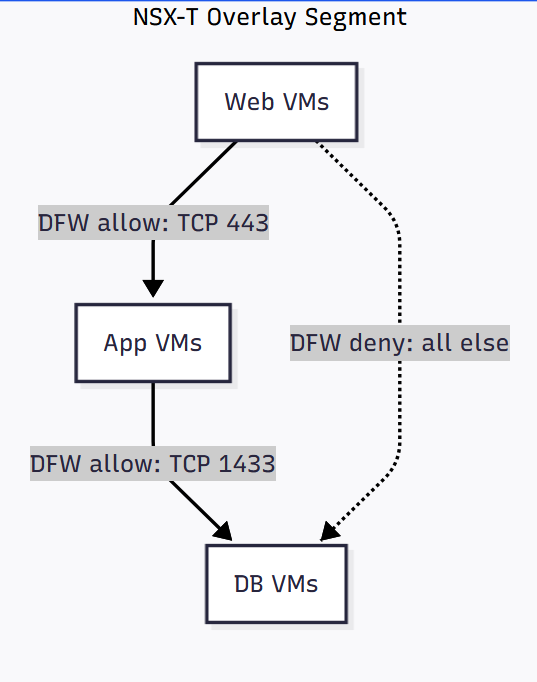
All VMs can live in the same segment, while DFW controls east-west traffic.
Pros
- Fine-grained security without VLAN sprawl
- Application-centric policies
- Easier audits
Cons
- Requires upfront design
- Poor tagging = poor security
- Troubleshooting shifts from “network” to “policy logic”
NSX-T should not be approached as a networking add-on. It fundamentally changes how infrastructure teams think about responsibility and ownership. When adopted intentionally, it simplifies operations and improves security.

