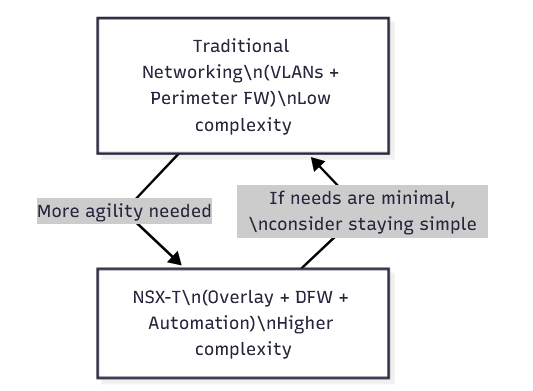
NSX-T is powerful – but not always necessary. In the right environment, it becomes the backbone of secure operations. In the wrong one, it can feel like extra complexity.
NSX-T is a great fit when:
- security requirements are strict
- east-west control matters
- automation and repeatability matter
- you need consistent policy across multiple clusters/domains
It may be overkill when:
- environment is tiny and stable
- changes are rare
- teams don’t have time to learn the model
- the priority is “keep it simple”
Pros
- Strong security posture without VLAN sprawl
- Consistent policy model for automation
- Enables modern app patterns (dynamic scaling, segmentation by intent)
Cons
- Requires skills + process maturity
- Poor governance creates operational noise
- Some environments don’t need this level of capability
NSX-T shines when you have complexity to manage and security to enforce at scale. If you don’t, it can be “too much platform” for the value returned. The best deployments start with clear goals, a tagging plan, and an operational model – not just installation.