Microsoft Defender for Cloud
Microsoft Defender for Cloud is a unified infrastructure security management system that strengthens the security posture of your data centers and provides advanced threat protection across your hybrid workloads in the cloud – whether they’re in Azure or not – as well as on premises.
- Strengthen security posture: Defender for Cloud assesses your environment and enables you to understand the status of your resources, and whether they are secure.
- Protect against threats: Defender for Cloud assesses your workloads and raises threat prevention recommendations and security alerts.
- Get secure faster: In Defender for Cloud, everything is done in cloud speed. Because it is natively integrated, deployment is easy, providing you with auto-provisioning and protection with Azure services.
- Policy compliance
Defender for Cloud is built on top of Azure Policy controls so you can set and monitor your policies to run on management groups, across subscriptions, and even for a whole tenant. - Security alerts
Defender for Cloud automatically collects, analyzes, and integrates log data from your Azure resources like firewall and endpoint protection to detect real threats. Then list of prioritized security alerts is shown in Microsoft Defender for Cloud along with the information you need to quickly investigate and remediate an attack. - Secure score
Defender for Cloud continually assesses your resources for security issues; then aggregates all the findings into a single score so that you can tell your current security situation.
Learn and SkillPipe content:
Defender for Cloud – capabilities
Policy Compliance – Run policies across management groups, subscriptions, or tenants.
Continuous Assessments – Assess new and deployed resources to ensure that they are configure properly.
Tailored Recommendations – Recommendations based on existing workload with instructions on how to implement them.
Threat Protection – Analyze attempted threats through alerts and impacted resource reports.
Learn and SkillPipe content:
Microsoft Sentinel
Microsoft Sentinel is a security information and event management (SIEM) solution that provides security analytics and threat intelligence across an enterprise.
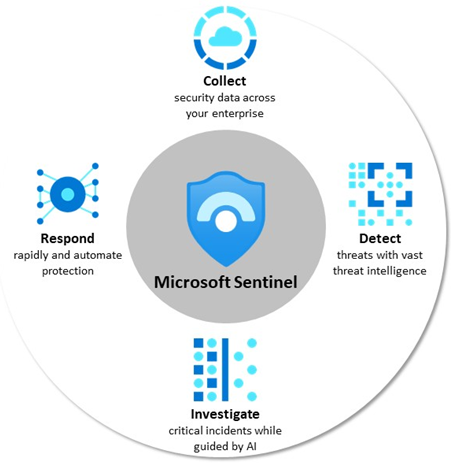
- Collect – data across all users, devices, applications, and infrastructure, both on-premises and in multiple clouds.
- Detect threats and minimize false positives using analytics.
- Investigate threats with AI and hunt suspicious activities at scale.
- Respond to incidents with built-in orchestration and automation of common tasks.
Learn and SkillPipe content:
Azure Key Vault
Azure Key Vault is a centralized cloud service for storing an application’s secrets in a single, central
location. It provides secure access to sensitive information by providing access control and logging
capabilities.
- Manage secrets You can use Key Vault to securely store and tightly control access to tokens, passwords, certificates, API keys, and other secrets.
- Manage encryption keys You can use Key Vault as a key management solution. Key Vault makes it easier to create and control the encryption keys that are used to encrypt your data.
- Manage SSL/TLS certificates Key Vault enables you to provision, manage, and deploy your publicand private Secure Sockets Layer/Transport Layer Security (SSL/TLS) certificates for both your Azure resources and your internal resources.
- Store secrets backed by hardware security modules (HSMs) These secrets and keys can be protected either by software or by FIPS 140-2 Level 2 validated HSMs.
Learn and SkillPipe content:
Azure Dedicated Host
Azure Dedicated Host is a service that provides physical servers – able to host one or more virtual machines – dedicated to one Azure subscription. Dedicated hosts are the same physical servers used in our data centers, provided as a resource. You can provision dedicated hosts within a region, availability zone, and fault domain. Then, you can place VMs directly into your provisioned hosts, in whatever configuration best meets your needs.
Limitations
– Virtual machine scale sets are not currently supported on dedicated hosts.
Benefits
Reserving the entire host provides the following benefits:
– Hardware isolation at the physical server level. No other VMs will be placed on your hosts. Dedicated hosts are deployed in the same data centers and share the same network and underlying storage infrastructure as other, non-isolated hosts.
– Control over maintenance events initiated by the Azure platform. While the majority of maintenance events have little to no impact on your virtual machines, there are some sensitive workloads where each second of pause can have an impact. With dedicated hosts, you can opt-in to a maintenance window to reduce the impact to your service.
– With the Azure hybrid benefit, you can bring your own licenses for Windows and SQL to Azure. Using the hybrid benefits provides you with additional benefits. For more information, see Azure Hybrid Benefit.
Learn and SkillPipe content:
Secure Network Connectivity
Defense in depth
A defense-in-depth strategy uses a series of mechanisms to slow the advance of an attack that aims at
acquiring unauthorized access to data.
You can visualize defense in depth as a set of layers, with the data to be secured at the center.
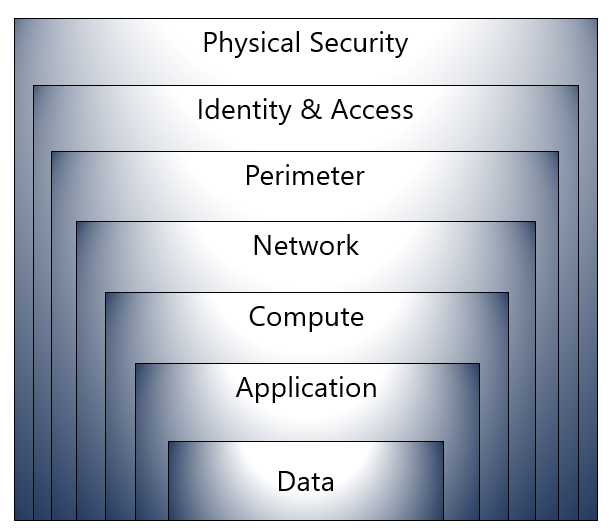
Here’s a brief overview of the role of each layer:
- The physical security layer is the first line of defense to protect computing hardware in the datacenter.
- The identity and access layer controls access to infrastructure and change control.
- The perimeter layer uses distributed denial of service (DDoS) protection to filter large-scale attacks
before they can cause a denial of service for users. - The network layer limits communication between resources through segmentation and access controls.
- The compute layer secures access to virtual machines.
- The application layer helps ensure that applications are secure and free of security vulnerabilities.
- The data layer controls access to business and customer data that you need to protect.
Learn and SkillPipe content:
Shared Security
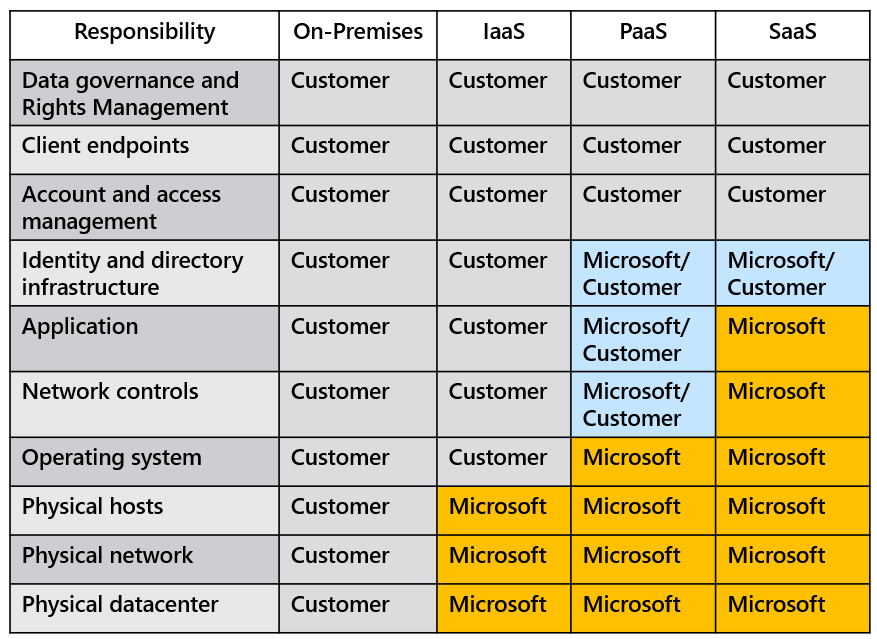
- Migrating from customer-controlled to cloud-based datacenters shifts the responsibility for security.
- Security becomes a shared concern between cloud providers and customers.
Network Security Groups (NSGs)
Network Security Groups (NSGs) filter network traffic to and from Azure resources on Azure Virtual Networks.
- Filters network traffic to, and from, Azure resources on Azure Virtual Networks.
- Set inbound and outbound rules to filter by source and destination IP address, port, and protocol.
- Add multiple rules, as needed, within subscription limits.
- Azure applies default, baseline, security rules to new NSGs.
- Override default rules with new, higher priority, rules.
Learn and SkillPipe content:
Azure Firewall
Azure Firewall is a managed, cloud-based network security service that helps protect resources in your
Azure virtual networks. A virtual network is similar to a traditional network that you’d operate in your own datacenter. It’s a fundamental building block for your private network that enables virtual machines and
other compute resources to securely communicate with each other, the internet, and on-premises
networks.
- Applies inbound and outbound traffic filtering rules
- Built-in high availability
- Unrestricted cloud scalability
- Uses Azure Monitor logging
Learn and SkillPipe content:
Azure Distributed Denial of Service (DDoS) protection
DDoS Protection identifies the attacker’s attempt to overwhelm the network and blocks further traffic
from them, ensuring that traffic never reaches Azure resources. Legitimate traffic from customers still
flows into Azure without any interruption of service.

- Sanitizes unwanted network traffic before it impacts service availability.
- Basic service tier is automatically enabled in Azure.
- Standard service tier adds mitigation capabilities that are tuned to protect Azure Virtual Network resources.
