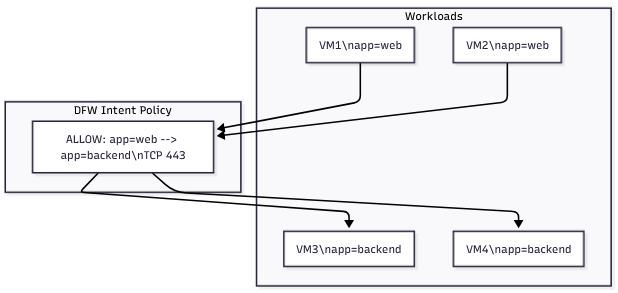
Distributed Firewall (DFW) is powerful, but it becomes truly scalable only when you stop thinking in IPs. IP-based rules still work, but they don’t age well in dynamic environments: VMs move, IPs change, autoscaling expands, and suddenly your policy becomes fragile.
The NSX-T mindset is intent-based security:
- “Web talks to backend on 443”
instead of
- “10.10.10.0/24 talks to 10.10.20.0/24 on 443”
Example: You add a new backend VM. With IP rules, you update firewall policy. With tags, you simply apply app=backend. Policy follows automatically.
Pros
- Policies scale naturally (no rule edits on scale-out)
- Clearer security intent for audits and reviews
- Works perfectly with IaC (Terraform/Ansible/GitOps)
Cons
- Tag governance is mandatory (or you get outages)
- Mistagging can open access or block production
- Requires naming standards and ownership rules
DFW is only as good as your tagging discipline. If tags are treated like a first-class asset (enforced, audited, standardized), NSX-T security becomes clean and resilient. If tags are ad hoc, you end up debugging policy more than traffic.