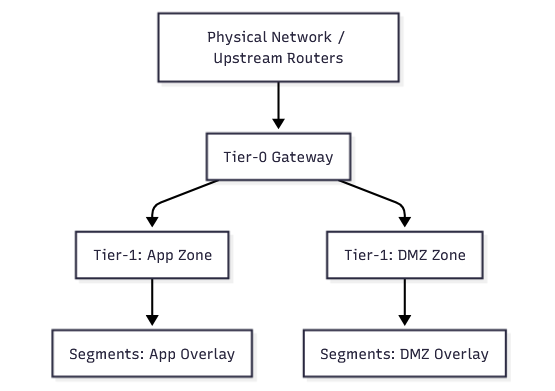
Tier-0 / Tier-1 routing is simple when you keep responsibilities clean:
- Tier-0 = external connectivity (north-south routing to physical network)
- Tier-1 = application/security domains (internal routing, localized control)
The moment you push too much app logic into Tier-0, troubleshooting and change control become painful.
A strong design uses Tier-1 gateways to isolate blast radius:
- Tier-1 for “App Zone”
- Tier-1 for “DMZ Zone”
- Tier-0 stays stable and boring
Pros
- Clear separation of responsibilities
- Safer change management (localized impact)
- Easier expansion (add Tier-1 domains cleanly)
Cons
- More objects to standardize (naming, ownership, lifecycle)
- Bad conventions lead to “object sprawl”
- Requires architectural discipline early
Tier-0/Tier-1 becomes messy only when teams don’t decide what belongs where. Keep Tier-0 focused on external routing, and use Tier-1 gateways to model security zones and app domains. Your future self will thank you.