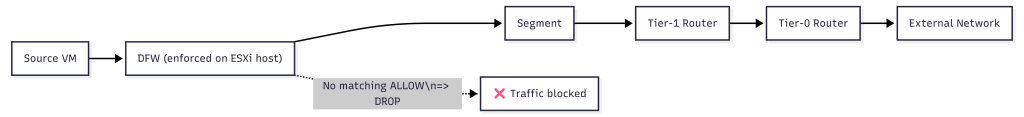
NSX-T troubleshooting feels different because you’re often debugging policy decisions instead of physical links. A typical packet journey is:
VM -> DFW -> Segment -> Tier-1 -> Tier-0 -> External
Most outages end up being:
- wrong group membership (tags)
- rule order/shadowing
- “applied-to” scope mistakes
- missing service definitions
A VM can ping its gateway but can’t reach an app on 443. Routing is fine. DFW rule is missing or scoped incorrectly. The win with NSX-T is that the platform can show you exactly where it was dropped – if you use the tools.
Pros
- Strong visibility (flow tools, rule hits, traceability)
- Deterministic enforcement close to workloads
- Less “mystery” behavior than physical middle boxes
Cons
- Requires policy literacy (order, groups, scope)
- Multiple layers can confuse newcomers
- You need process: tagging, naming, testing, rollbacks
NSX-T troubleshooting rewards structured thinking. If you follow the flow and validate group membership + rule scope first, you’ll fix problems faster than in classic networks.
